Why Thola?
With the increasing number and variety of platforms and applications organization utilize and the amount of data being generated by those platforms, cyber threat landscapes by default will continue to expand. An organizations ability to defend itself quickly and effectively against targeted attacks from known and unknown sources is a challenge no matter your size. In order to be secure and protect your most valuable organizational assets, you will need to take a proactive approach to detecting and responding to cyber threats.
Your process of detecting and quantifying threats should be automated and aligned with tools, tactics, and procedures (TTPs) of attackers. An ideally implemented threat detection strategy should include measures to discover and respond to threats quickly enough to minimize the impact.
How does our solution help?
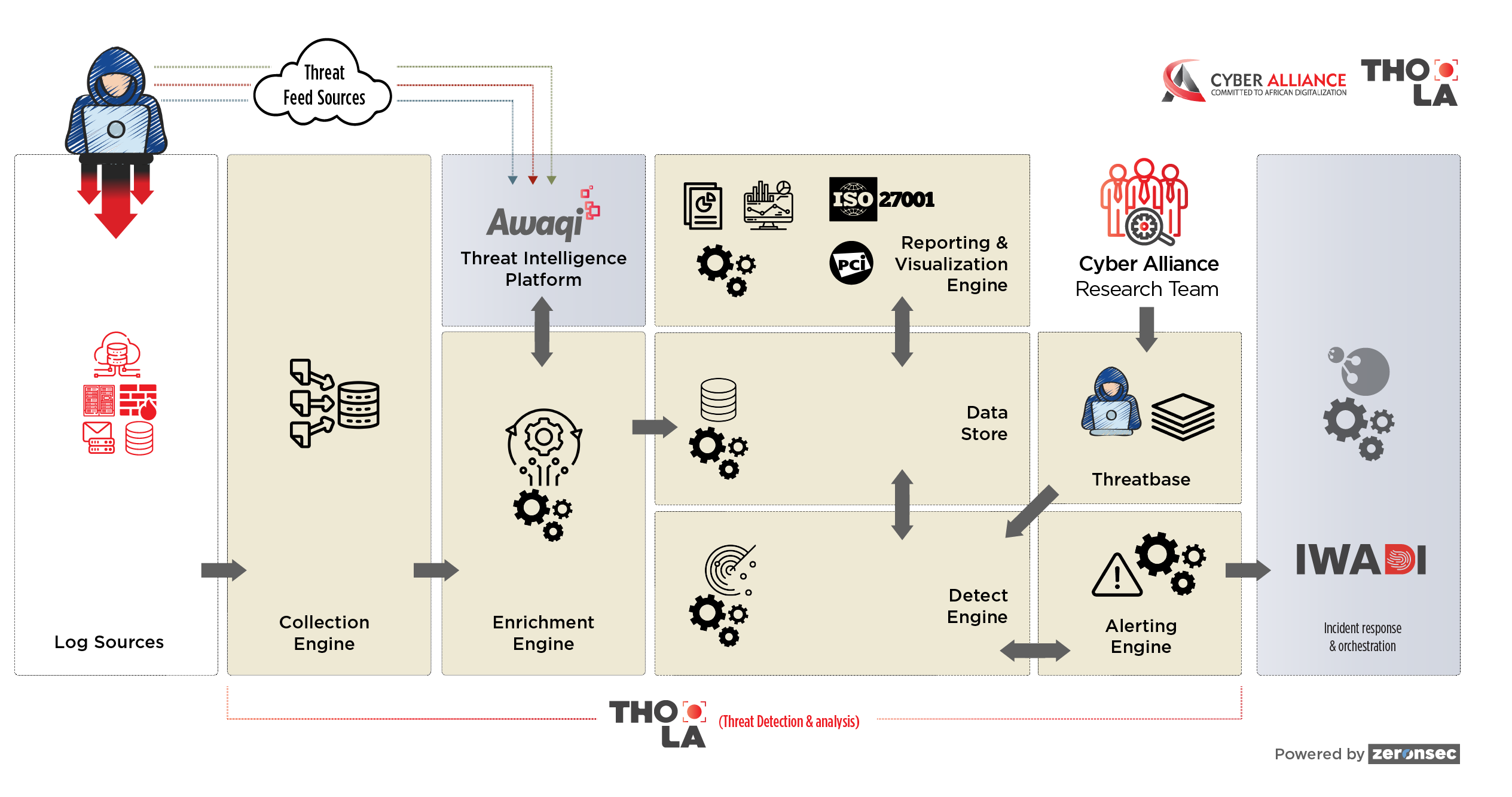
Thola is a Big Data based threat detection and analytics platform that can seamlessly integrate within various aspects of your tech environment to help you detect, monitor, and respond to cyber threats in near real-time. We have a unique Threat-base library that runs on top of Thola that follows cyber kill chain and MITRE ATT&CK frameworks to effectively detect cyber threats. Many organizations compliment the threat detection and mitigation capacities of Thola with CyberAlliance's threat intelligence platform Awaqi that is designed to gather high-quality threat intelligence data to consistently mitigate cyber threats.
Solution For Major Challenges
Alert Fatigue
Due to huge volumes and varieties of events and alerts, customers find it challenging to cope with it. Thola helps you deal with it effectively with out-of-the-box threat detection rules based on frameworks enabling you to focus on more meaningful and actionable alerts.
Traditional Detection Approach
Historically, the approach for threats detection is reactive and is based on individual alerts, which doesn’t provide complete context of the attacks. Thola comes with behaviour-based rule base libraries which keeps updating as attackers change their tools, tactics and procedures to detect threats in the environment at various stages of their lifecycle.
Ineffective Threat Visualizations
Security analysts find it challenging to visualize and understand the threats to their environment as it requires lot of configuration on analytics tools to build new visualizations. Thola comes with pre-defined visualization dashboards to understand the current picture with local filters and real-time view to drive the analysis effectively and efficiently.
Threat Hunting Capabilities
Traditional SIEM platforms takes much time to apply the queries and hunt for the threats on historical data. As Thola is built on Big Data based technologies, it helps analysts run their queries quickly, hunt for the threats and build the visualizations with ease.
Value For The Customer
- Enables CISO’s to align threat detection and analytics platform investments to the reality of cyber threats.
- Makes analyst’s life easier, threat detection rules and easily understandable visualization dashboards running on top of data helps identify threats in near real-time. They can define relations among multiple entities (assets, IOCs, network and previous incidents) to ensure they have better control of the environment.
- Has capabilities to monitor critical files present in systems.
- Built on big-data based technologies, it runs your queries much faster and presents you the output in seconds even for years-long query timeframes.
- Visualization dashboards to understand threats landscape.
- Helps categorize the incidents by providing additional context of assets, networks, threat intelligence and vulnerability data.
- MITRE ATT&CK™ and Cyber Kill Chain ® based visualizations and alerting.
- Integrates with any data source with structured, semi-structured and unstructured data.
- Collects network flow data and packets to detect the threats at network level and help resolve the operational issues.
- Provide threat hunting and free-text searching capabilities to users for operational and security monitoring.
TRUST SCORE
CyberAlliance's Cyber Trust Score is a powerful risk assessment tool that can help small and medium-sized businesses identify and manage cyber threats while also helping financial services firms assess investment and lending risk. Enterprises can also use the Cyber Trust Score to manage supply chain risk. With our objective risk assessment tool, you can identify vulnerabilities, improve your security practices, and meet or exceed industry standards. By enhancing your cybersecurity posture, you can build trust with customers and partners, boost your reputation, and unlock new opportunities for growth. Don't let cyber threats hold you back. Trust in CyberAlliance's Cyber Trust Score to position your business as a trusted partner in the marketplace.
Find out for yourself why the Trust Score sets the standard in Cyber Security Risk Rating and Third-party Cyber Risk Mitigation



