Why Awaqi?
Today’s cyber adversaries have intelligence about the target(s) and good knowledge about advance TTPs (Tools, Techniques & Procedures). With the kind of financial support they have, they are capable of launching extremely sophisticated attacks on their targets. The techniques used are so advanced that not only the end user, but even the implemented security controls cannot detect them.
This is possible because the intelligence these adversaries gather is accurate and precise. With the help of this knowledge they are able to customize their TTPs. The tools are designed and developed in such a way that the attacker’s behaviour or presence remains anonymous or appears absolutely normal within the target’s environment they can remain undetected. Therefore, understanding the attacker’s TTPs and their origins is crucial for detecting threats in your IT environment.
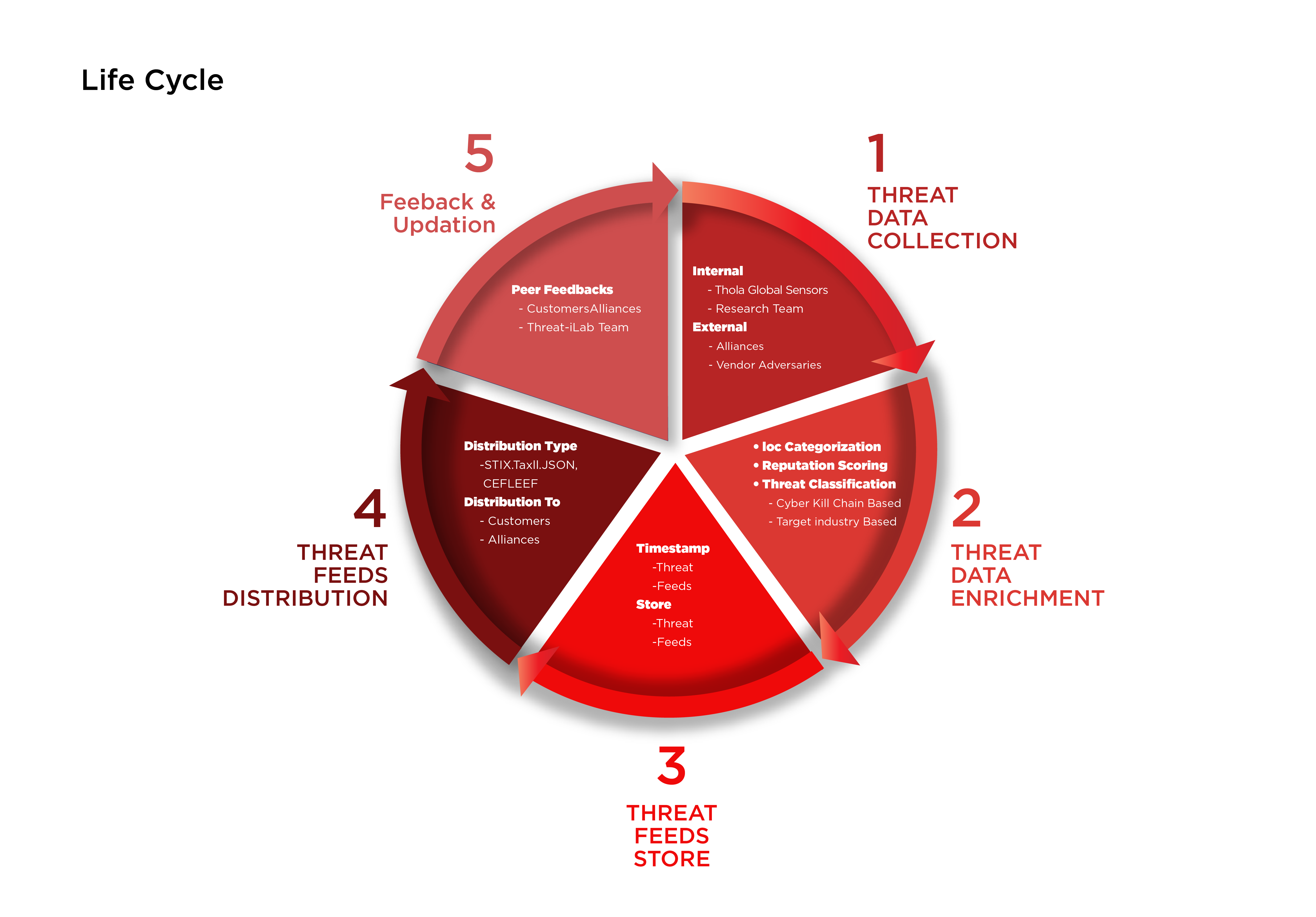
This is where Cyber Alliance’s Threat Intelligence solutions come into play. We have up-to-date knowledge about the possible threats. We gather high-quality threat intelligence, from reliable sources and sort and enrich the data to make it more meaningful and actionable.
Benefits
- Visibility of malicious communications happening with threat entities
- Geographical representation of cyber threats
- Reputational score-based threat monitoring
- Real-time visual representation of attacks
- Greater control of your threat risk inventory
- Detailed visualizations of internal infections
- Categorized monitoring of cyber threats and infected assets
- Identification of the riskiest internal assets due to cyber infections
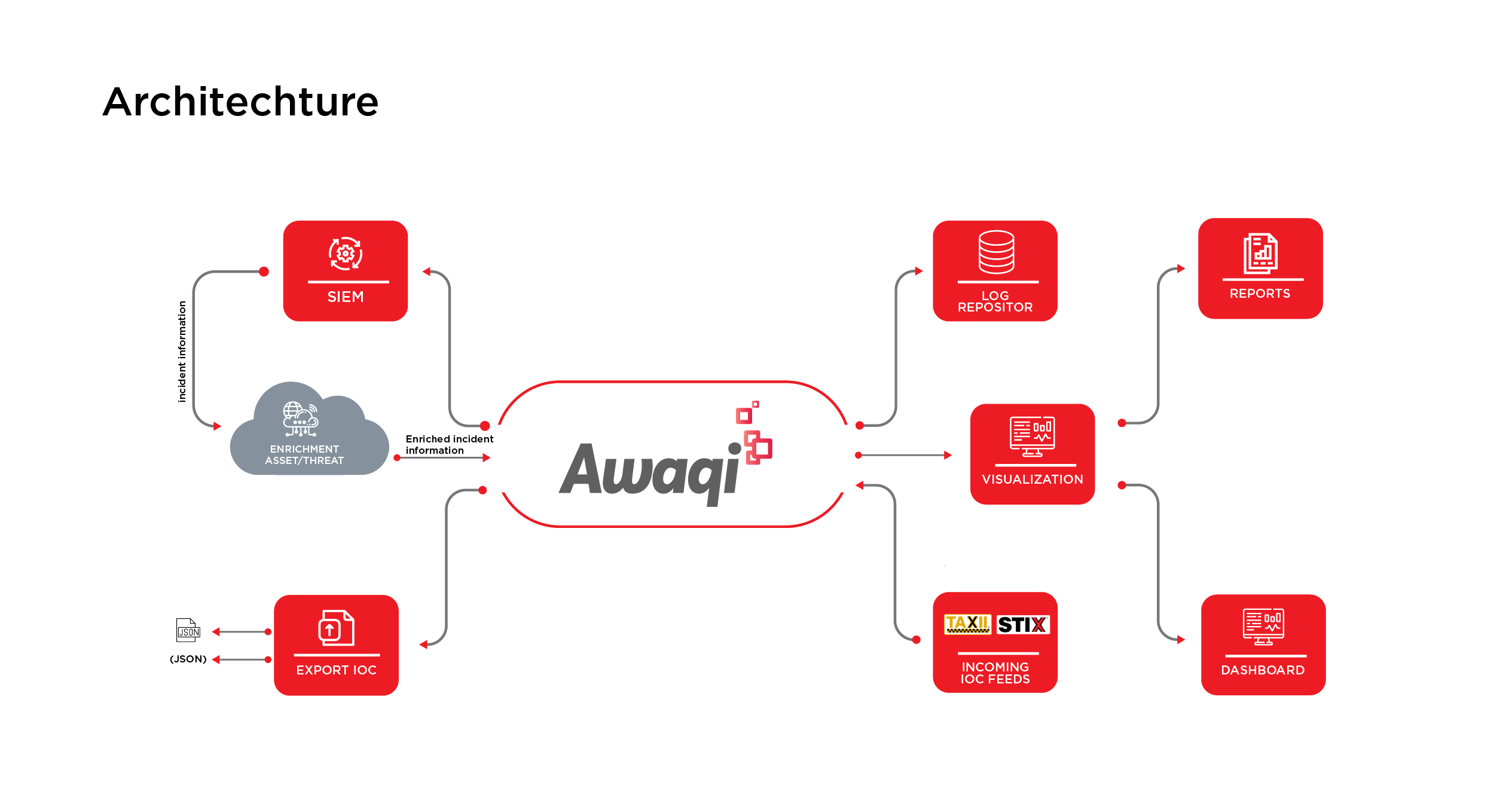
Awaqi Solves For Common Challenges
Alert Fatigue
Due to huge volumes and complexity of threat feeds, customers find it challenging to cope with them. Awaqi helps you effectively deal with these threats with built-in features like de-duplication, enrichment and aggregation, enabling you to draw meaningful and actionable intelligence.
Lack of staff expertise
Historically, the approach to threats detection is often reactive and based on individual alerts. This approach does not provide full context of cyber attacks. To detect cyber threats in your environment at vaious lifecycle stages, Awaqi is equipped with behavior-based rule base libraries that constantly update as attackers change their tools, tactics, and procedures.
Awaqi provides organizations a view of infection(s) in real time, and includes world map locationing to make it easier for your staff to acquire more insight on your attacker.
Awaqi can be integrated with other platforms in a matter of a few clicks.
Unaware Senior Management
Awaqi gives you a highly customizable and user-friendly interface that allows even a novice to adapt and learn it in few days.
Threat Feeds
Ransomware Feeds
A set of ip addresses domain and URLs with context for ransomware establishments.
Tor Node Feeds
A set of ip addresses TOR network connections.
Malware Feeds
A set of ip addresses and domain with context for malware connections.
Phishing Feeds
A set of URL with context for pushing attacks.
Malicious Hash Feeds
A
set of malicious Hash Values.
TRUST SCORE
CyberAlliance's Cyber Trust Score is a powerful risk assessment tool that can help small and medium-sized businesses identify and manage cyber threats while also helping financial services firms assess investment and lending risk. Enterprises can also use the Cyber Trust Score to manage supply chain risk. With our objective risk assessment tool, you can identify vulnerabilities, improve your security practices, and meet or exceed industry standards. By enhancing your cybersecurity posture, you can build trust with customers and partners, boost your reputation, and unlock new opportunities for growth. Don't let cyber threats hold you back. Trust in CyberAlliance's Cyber Trust Score to position your business as a trusted partner in the marketplace.
Find out for yourself why the Trust Score sets the standard in Cyber Security Risk Rating and Third-party Cyber Risk Mitigation
.svg)






